LMNTRIX
RESOURCECENTER





FEATUREDRESOURCE
The Story of Carlo Minassian and LMNTRIX
LMNTRIX Active Defense Datasheet
Active Defense (MDR) Case Study – Finance Sector
Turning Inward – A White Paper by LMNTRIX
Market Guide For MDR Services 2020
The Story of Carlo Minassian and LMNTRIX
LMNTRIX Active Defense Datasheet
Active Defense (MDR) Case Study – Finance Sector
Turning Inward – A White Paper by LMNTRIX
Market Guide For MDR Services 2020
RESOURCE
[wpdreams_ajaxsearchlite]
-
All -
Videos -
Analyst Coverage -
Infographics -
Case Study -
Data Sheet -
White Paper

Why Your SIEM Might Be As Useful

The Story of Carlo Minassian and LMNTRIX

Demystifying XDR – Common Myths & Realities

The five pillars of a modern security

Why SOCs Fail

How Mitre-Attck can be mapped to finished
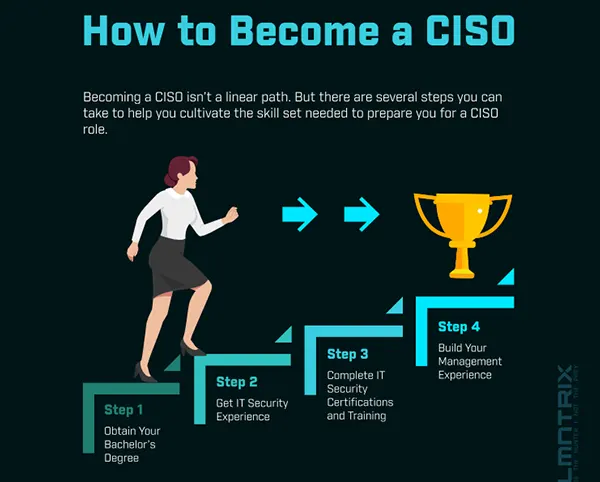
How to become a CISO what a

Red Team Case Study
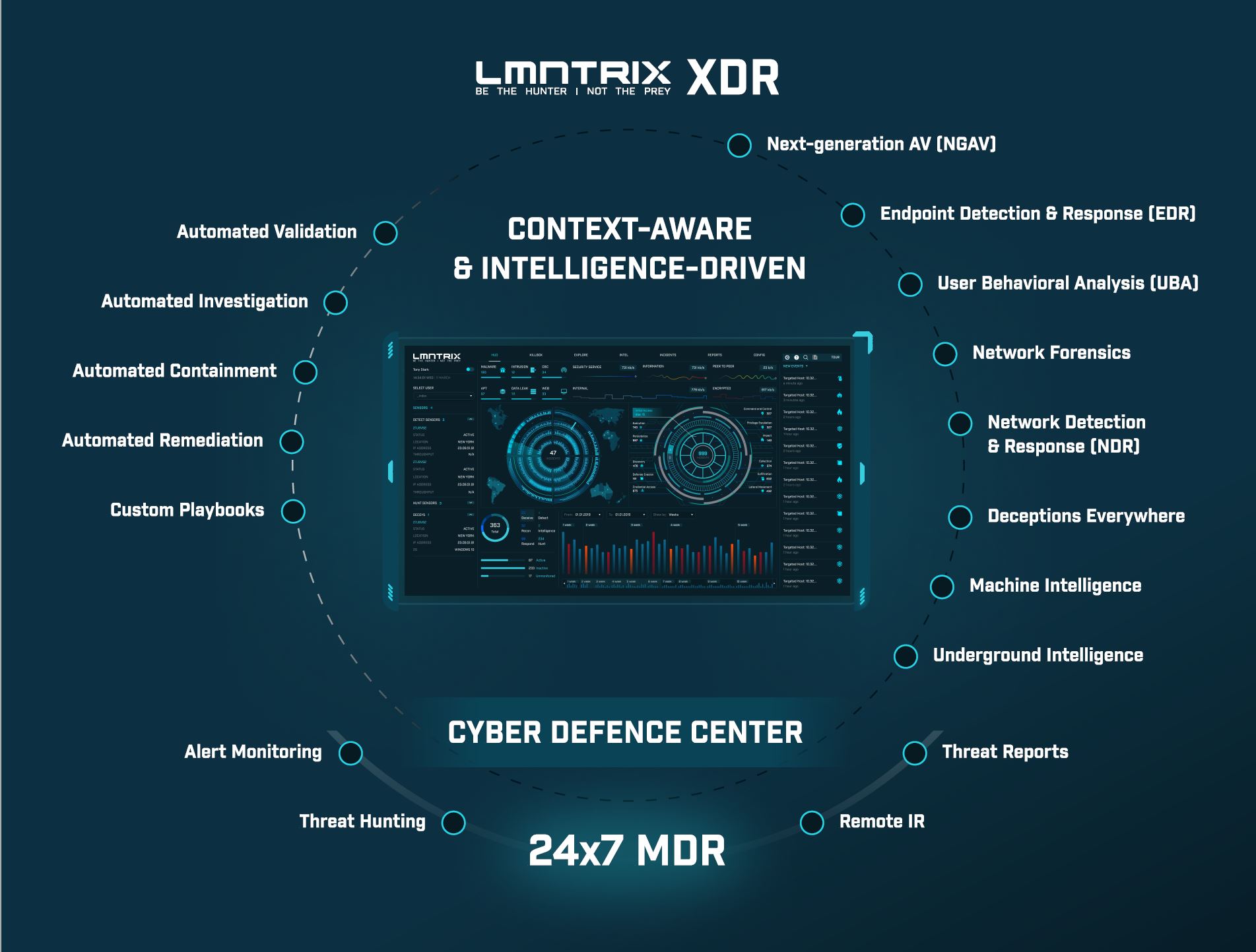
LMNTRIX XDR Datasheet

LMNTRIX Active Defense Datasheet

Identity Protection In a Digital World: A

Securing The Cloud : A Comprehensive Guide

How Machine Learning & Underground Intel Augment

Active Defense (MDR) Case Study – Finance

SOC Modernization and the Role of XDR

Unveiling The Power of LMNTRIX Mobile Threat

Industrial Control System Security Guide

EDR : Putting The X Factor in

Network Detection and Response with LMNTRIX XDR

Deception Technology Guide

Business Email Compromise: A Billion-Dollar Problem

Ransomware Protection, Containment, And Recovery Guide

You’ve Been Hacked! Now What? How to

What Does It Really Cost to Build

Business Heads in the Security Clouds

The Future of Machine Learning in Cybersecurity

Thinking of Starting a Adversary Hunting Program?

10 Habits of Effective SOCs and How

How to Select an MDR Provider?

Turning Inward – A White Paper by

Market Guide For MDR Services 2020
Market Guide For MDR Services 2019
XDR Buyer’s Guide

Automated Attack Validation Buyer’s Guide

Real Time & Automated Attack Validation Platform

Why Your SIEM Might Be As Useful

The Story of Carlo Minassian and LMNTRIX

Market Guide For MDR Services 2020

Market Guide For MDR Services 2019

Demystifying XDR – Common Myths & Realities

The five pillars of a modern security

Why SOCs Fail

How Mitre-Attck can be mapped to finished

How to become a CISO what a

Red Team Case Study

Active Defense (MDR) Case Study – Finance

LMNTRIX XDR Datasheet

LMNTRIX Active Defense Datasheet

Real Time & Automated Attack Validation Platform

Automated Attack Validation Buyer’s Guide

XDR Buyer’s Guide

Turning Inward – A White Paper by

How to Select an MDR Provider?

10 Habits of Effective SOCs and How

Thinking of Starting a Adversary Hunting Program?

The Future of Machine Learning in Cybersecurity

Business Heads in the Security Clouds

What Does It Really Cost to Build

You’ve Been Hacked! Now What? How to

Ransomware Protection, Containment, And Recovery Guide

Business Email Compromise: A Billion-Dollar Problem

Deception Technology Guide

Network Detection and Response with LMNTRIX XDR

EDR : Putting The X Factor in

Industrial Control System Security Guide

Unveiling The Power of LMNTRIX Mobile Threat

SOC Modernization and the Role of XDR

How Machine Learning & Underground Intel Augment

Securing The Cloud : A Comprehensive Guide

Identity Protection In a Digital World: A
Download OurDatasheet
LMNTRIX® NEWS

Jan 25, 2024
Zero-Day Exploits : Lessons Learned From The GhostShell SQL

Sep 22, 2022
LMNTRIX Has Been Named One Of The Top 250 MSSP Companies

